Introduction

So, I managed to participate in Malaysia’s Cybersecurity Camp (MCC) 2023! But hold up, what is MCC? MCC is an initiative that focuses on developing a better cybersecurity community for the next generation. It involves networking with top local cybersecurity experts, facilitating student exchanges to build lasting friendships, and enjoying educational experiences in nature. The camp aims to identify talented individuals, increase their knowledge through expert guidance, close the talent gap between students and professionals, bring students to par with global peers, and produce graduates ready for the workforce with minimal training. It is organised by NanoSec and RE:HACK Consultancy , it’s a community-driven effort by IT security professionals and students.
So that said, what was MCC2023 like? Well, IT WAS AWESOME!!!! Before I begin to share my experience in MCC2023, I have to start from the beginning as it involves a lot of help from a lot of people. In 2022, I heard of MCC and I was enthusiastic to join. However, I had exams and classes at the time, so I thought MCC wasn’t worth skipping classes and exams. Oh I was sooooo wrong.
Sometimes we thought but never think and sometimes we think and never thought
Registering for MCC2023
However, after joining my university’s cybersecurity club, Forensic & Security Research Center Student Section (FSEC-SS), where I surround myself with like-minded people, I feel that my classes are worth skipping. For that reason, I decided to register for MCC2023! The journey to register is easy, just fill in a form and let fate take its place as you can only go to MCC if you are chosen. However, I did have help at the time and call me whatever you want but I love my friends. They helped me in some ways during the registration process and as well as the interview process. These are my friends:
- Yeo Jia Qi (MCC2023 crew)
- Kelvin Teo (MCC2023 crew)
- Loh Kae Shyan (MCC2023 crew)
- Chang Shiau Huei (MCC2022 crew)
Furthermore, after the registration they gave us a TryHackMe box to do. Basically, they were testing our knowledge and skills. This is the box if you want to try. The box involves a blue teaming path as well as a red teaming path. Being a purple teamer, I did both heheheh.
The Interview for MCC2023
Wait, wait, wait… There’s an interview process??? Yes there is! So after the registration, RE:HACK will shortlist the participants and interview them to see whether it’s worth taking them into MCC. Plus, the whole camp was sponsored so in their point of view, they have to choose the participants wisely. So, beforehand Jia Qi was kind enough to give me some pointers on what to say during the interview. However… the day of my interview was the worst timing ever. In context, RE:HACK will organise sharing sessions sometimes and it is a good initiative for people who want to learn about certain topics. However, on the day of my interview, there was a sharing session by Teng about reverse engineering which I was very interested in and Jia Qi also invited me to it, but the timing though…
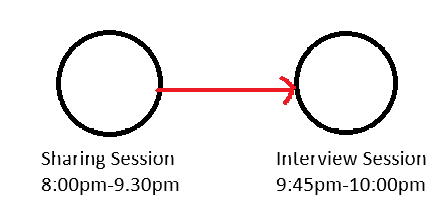
Now I just want to point out, no one is at fault, it was just a coincidence that both sessions were close to each other.
So, I was interested in reverse engineering so I tried my best to concentrate and learn as much as I can from the King of Reverse Engineering. By the end of the session, I was blur and tired. For that reason, during the interview session, I missed out some parts on what to say which Jia Qi was like:

Anyways, months passed by and… I managed to get into MCC2023!!!
Day 1 - The Journey Begins

Just want to point out, this picture is by RE:HACK pretty awesome isn’t it?

So, on the 8th of December at 8 am in the morning Roheen, Darrshan and I took a road trip together to Port Dickson to start our MCC journey! It was a fun one and a half hour drive there. We played songs and vibed in the car.
I’ll be honest I don’t remember much of what we did in the car because I fell asleep… But we did point at the Port Dickson sign and screamed “PORT DICKSONNNN”

Anyways, a good one and a half hours later, we reached the resort! We put our luggages aside and talked to each other because funny enough we were the first ones there lmao. So, we waited around 15-30 minutes for the rest who coming by bus to arrive.

Once everyone arrived, we settled down in a small room to register where we got some MCC swags which was pretty cool. We got a shirt, a bag and some stickers. We then started networking with each other! From there, I found out that one of my Forensics challenge from ASEAN Battle of Hackers made a participant reformat their laptop… it was uwu… it had malware…
This is where I met my roommate as well, Shen. A OSCP and as well as a OSWP holder. I asked some questions on how the OSCP was and his advice on taking the certification. He said as long as you complete the labs for Active Directory, everything is good.
Well to me, this networking session was more of a chit chatting session which was nice because I was FINALLY surrounded by like-minded people!

Anyways, once the speakers arrived, we went back to our places and Mr Ahmad Ashraff began introducing us to MCC, why he organised MCC and who sponsored this year’s MCC. After his speech, we had Rizki Boisandie, a career advisor who gave some advice on how to get a job in the cybersecurity industry. We even spoke to him after the session for more advice and I have to say his advice is pretty insightful!
After that, we had lunch and we were free to do whatever we wanted to do until tomorrow

BUT WAIT!!! Because before we left for lunch, the crew of MCC gave us an assignment or rather in my case, a mission (basically a CTF challenge). This year’s assignment is a reverse engineering challenge which was made by our handsome and wonderful challenge creator Teng! Remember him btw.

If you know me well enough or no… if you know any cybersecurity enthusiast that does CTFs, you know that we have a TRY HARDER mentality. So, we gather our minds and did the challenge… until 2-3am.
yupp.. that was us discussing about the challenge…
What’s funny is that they assigned us to different groups, but we didn’t discuss the challenge with our group mates. Instead, people from each team came together me included, to discuss the challenge.
I remember I was in a room with 5 other people from different groups discussing about the RE challenge but all of us don’t specialise in RE
Day 2 - King of Forensics Meets the God of Forensics

The next features a DFIR workshop from none other than Fareed Fauzi who I consider one of the God of Forensics. I consider myself to be average in the field but everyone calls me the King of Forensics so I’ll leave it that way heh.
“But Zach, if you’re average why did you join this workshop?”. Well, I believe if you know 80-90% of the subject, it is good to pick up another 10-20% from someone who knows more than you do. In cybersecurity, we’re always learning. Don’t forget that, even if it’s a small amount information, you’re still learning.

Of course… Barney had to tag along
Anyways, during the workshop we learned mainly about Windows Forensics and artefacts we can find within Windows. So, what was the 10-20% things that I learned? Well, I learned:
- When doing acquisition, putting the hostname as the filename is a standard
- When analysing hard disks, it’s better to mount it and do a triage on it first as it gathers and extracts most of the information from the disk first instead of extracting it one by one from Autopsy
- When analysing logs, there is no easy way but to analyse them one by one, unless you use Hayabusa
- When doing Blue Teaming, you have to know Red Teaming strategies so being a Purple Teamer is the way to go (YES, I MADE A GOOD DECISION)

Also, I got to coach two of my juniors, Emmy and Wei Ying, I hope I explained the things that Fareed was talking about clearly to them, but overall we had a fun time talking and learning together.
Just want to note, we were talking the entire session and I think I was being too loud… Sorry Fareed XD
Overall, we had fun and we learned something from the session, which is my motto for every CTF ever. Learning is supposed to be fun, don’t compromise that. Also adding to that point, as I did some of Fareed’s challenges before, I asked him as a challenge creator how does he make his challenges. The answer was not what I was expected. He said that he tries to learn about stuff when making challenges and that’s what I do as well. So, it’s good to hear I’m on the right track!
Oh yea, it’s worth mentioning, during the lunch break, we managed to find one of the three flags for the reverse challenge, all thanks to our Prompt Engineer Firdaus!! Then, after the lunch break, Shenghe managed to find another flag which we all got excited for. If you want the wrong way of solving the challenge, well the write up of the challenge is coming soon.
It is not the correct way of solving the challenge, do not use it to learn reverse.

Later that night, we met the founder of FSEC, Max. Max held a mini workshop that night about lock picking, which was something new for me to do. However, with the guidance of Solomon and Darrshan, I managed to unlock (see what I did there?) a new skill.
From what I heard, Max founded FSEC and did weekly workshops so that the whole FSEC could go to DEFCON one day. I was like WHATTTTTT

After the session was over, me and Solomon went on trying to find the final flag of the reverse challenge. You might be wondering… did we get the flag? YES WE DID!!! He was screaming in my ear when he got the flag. We hugged and celebrated that we finally got all 3/3 of the flags.
Also, while solving the challenge I almost destroyed all of our computers as I thought I found something and I grabbed Solomon’s hand and shook it not knowing he had a bottle of water in his hand and… he screamed like R2D2.

After the whole day, we were tired and hungry… So what do you do when you’re hungry? You walk 2km to the nearest burger joint to get Ostrich Burgers!!! Me, Roheen, Darrshan, Solomon, and Shenghe walked all the way to the burger stall and we had the best time talking, walking and in the end we had a blast!
Day 3 - Purple Teamer is Red Teaming

The next day featured a Red Teaming workshop, adhering to my Purple Teaming principles during the camp where we have Shahril and Faeq teach us how to do Red Teaming in a real life scenario. This workshop features a mini boot2root challenge which we had fun doing. However, the challenge features a RCE vulnerability in a web app which Roheen exploited and managed to accidentally deface the web page which had the vulnerability. This made exploiting the box impossible for everyone else lmao. (but they fixed it so no worries)

Roheen celebrating his mistake with Barney XD
In addition to the boot2root challenge, we managed to touch (at the time of writing) a new Command and Control (C2) server called Sliver. It was pretty cool to be able to learn a new C2 server which is used in Red Teaming situations. We learned what were beacons and how to control those beacons.
Overall, the session was quite fun and insightful to me as a purple teamer. So, as a Purple Teamer, what was the thing I learned from this workshop? Well, I mainly learned:
- How to use Sliver, the C2 server
- What happens with SOC detects you?
- Red Teamers will try to avoid being detected
- But if they got caught, they will try another method
- Blue Teamers will call if you get caught but otherwise they need to update their rules

After the session, we decided to go to the pool to have some fun and Nal almost drowned. Thankfully, he survived.

After a good swim and some lessons learned (like not to go into the 2.6m swimming pool), we had a good BBQ with some good conversations. That’s where I learned that Nal is my rival! He was in the Petronas Inter-University CTF 2023 and as well as the PWC’s Hackaday CTF 2023. We (DinoDefend3rs during PWC and HC4 during Petronas) managed to beat them during these 2 times.
Just want to say Nal. If you’re reading this, all the bombastic side eyes was a joke, I respect you as a CTF player and the passion you have to grow the cybersecurity community in your university.

To end the night off, Roheen, Darrshan and I played some pool which I severely injured my finger when I was breaking. Well, not only managed to break the billiard balls but I also managed to break my own finger, but hey we won so nothing else matters lmao.
Day 4 - The Journey Has Just Begun
Welp here we are, the last day… I really feel sad leaving the people who can call friends, the people who I can vibe with within the cybersecurity industry.

Nothing really happened during the last day, we packed, we ate and we left.
BUT WAIT!!! Not before a final picture together!

Honestly, to end this blog post off, I would like to thank Mr Ahmad Ashraff, NanoSec and RE:HACK for offering me this opportunity to learn and grow in this community because I finally found a community which I can vibe and learn with. Lastly, I would love to shout out to Jia Qi for her continuous support and guidance before the camp. She is a great friend who will believe in you and support you until the very end.
here’s a flag for you MCC2023:
flag{!M_GoiNG_7o_M1Ss_MCc2023}