
Introduction
While Malaysia is going through the One-By-One incident, Singapore is having a cybersecurity conference called Off-By-One organised by StarLabs! Like any cybersecurity conference… in Singapore, it is filled with plenty of talks from people who are willing to share their technical knowledge and experiences. However, what makes this conference different is that every talk is based on Red Teaming, specifically Vulnerability Research.
I first heard of Off-By-One in BlackHat Asia 2024 where Belinda was asking people to join Off-By-One as speakers. Remember her by the way, she’s an important person in this blog post. Belinda mentioned that Mr Yapp from RE:HACK had requested for 2 tickets for 2 MCC Alumni. Knowing Mr Yapp had already sponsored me for not only one but two events, I knew it wasn’t me. In all honesty, I have benefited a lot from the sponsorships and I am grateful for it. So, it’s time to let other people benefit from it instead of lil old me.

Learning From Undertale
Undertale is an RPG game made by Toby Fox, the game is centred around the concept of DETERMINATION!!! So being determined to go to the conference, I asked Belinda, one of the people who help organise cybersecurity conferences such as this, whether there is a student sponsorship program like the one I got for BlackHat Asia and she said she plans to do something like that. However, getting an update from her later on reveals that the student scholarship will be done next year in 2025.

However, I have been told by my friends that I have a 大胆 personality, so I thought to try my luck whether I could get a ticket anyways. So, I asked Belinda if I could get a complimentary ticket and she said she’ll try. So, I waited… and waited… and waited… until it was one week before the conference.
At that point, I kinda forgotten about it because who am I to demand for a free ticket? Anyways, I was having dinner with Shiau Huei, Choo, Robbin, Shenghe and Shen (felt out of place for being a noob) and I received a message!
Basically, when I saw that message I screamed:
me: I GOT TICKETS TO OFF-BY-ONE!!!!
And everyone at the table was like:

yes, my blog has GIFs now. (not the soap, not the peanut butter, nvm just keep reading)
By the grace of God, she helped me out. Of course this shall not be forgotten, I’ll pay it forward by helping out other people in the future and share what I have learned there (wew I just broke the fourth wall) but for now thank you Belinda!
Day 1: God Gives His Toughest Battles to His Strongest Soldiers
Now in context, I have completed final semester in university. What does that mean? Well it means unlike BlackHat Asia and SINCON, I can finally go to a conference stress free! Right? RIGHT? Well no.

Off-By-One was going to be held on the 26th to the 27th of June, and I have to go down to Singapore on the 25th of June. However, on the 24th of June, there was a SANS Community Night in Malaysia. Ah yes, the many people who saw me that day noticed I was out of it. Basically, I had stomach issues and a massive headache, which carried over to the next day. It was as if God was trying to punish me for telling my juniors that I couldn’t relate to assignments, classes and exams because I “graduated”. Anyways, the point is that I went to Singapore sick.
Shakespeare Was Here?

So, they say first impression matters right? Well, if Off-By-One was a person, he (or she, I’m not sexist) sure did made a good impression by giving us this amazing electronic badge which was designed and made by StarLabs, as an entrance pass to the conference instead of the usual name cards. Anyways, when I first saw this on LinkedIn when Off-By-One announced it, that filled up my DETERMINATION!!! Because similar to Global Cybersecurity Camp or GCC (ughhh the pain….. foreshadowing later) and SINCON, these electronic badges had CTF challenges in them! In the same LinkedIn post, they also mentioned that there is a competition involved and the winner will get a Nintendo Switch!
When I first got to the conference, as usual they asked for my name, and as usual I always forget which name I gave them. Whether it was Zach or my real name. Anyways, when they found my name, the conversation taken place was like an reenactment of Shakespeare’s quote “to be or not to be” but instead it was “to give or not to give”:
dude 1 to dude 2: THERE ARE FREE PASSES? Should we give him?
dude 2: oh that one is by Belinda, yea you have to give him.
Anytime in these kind of blogs, I should really keep a thank you counter because first of all, I couldn’t have done a lot of stuff without someone’s help. Secondly, it’s funny. With that said, thank you once again Belinda for your name helped me HAHAHAHAHAHA.
However, Belinda was REALLY busy, she was one of the organisers of the conference. So, it was pretty reasonable that she didn’t have the time to introduce me to people there. But her colleague, Mei Ling was there to guide me around! She was also the one who sent out the complimentary ticket to me before the conference, so it was cool seeing her there!
SPITTING FACTS

So, for those of you who don’t know, in any of these kind conferences there will be an opening keynote. As I came in late, I missed out on a few stuff. However, when I finally popped in, the current talk was by Dr Silvio from InfoSect who was speaking about “Breaking Into Vulnerability Research”. Now normally opening keynotes at conferences are boring. I kid you not, every time a conference agenda says [OPENING KEYNOTE], I would normally walk out the room halfway into the keynote.
However, for Dr Silvio’s opening keynote, it was pretty interesting because it wasn’t the usual, “oh, we need to improve this cybersecurity thing!” or “here’s my product, it’s good!”. Okay, to be fair, he did market his company but it did make an impact on me. How? Well, first of all he was saying that you as the founder of a cybersecurity startup or anyone who is managing the main part of your cybersecurity startup, basically your team lead, must be specialised or in other words technical. Looking at his slides and hearing that, I was like, YES! YES! YES! IT SHOULD BE LIKE THAT!!!

Oh it just reminds me of the many people who I have heard of and that one time when I met a very famous cybersecurity CEO and [INSERT PRONOUN HERE] famous line was:
person: I'm not a technical person (3 times)
me: (thinking internally) i'm not even asking technical questions.
yea… I’m not in the mood to get sued, so just treat it as if I respect the person’s gender.

Any many ways, another thing that Dr Silvio did that made an impact on me was that he made me love pwn challenges and vulnerability research in general. He mentioned the kinds of people they hire which includes CTF players and Digital Forensics experts! Furthermore, he also mentioned it’s better for researchers in their company to be physically there so that people actually know who you are, you can learn from other people and basically perform better there.
Single JSON Object

Ah another conference another encounter with the JSON list, but this time my friends weren’t around. So, that makes that a single JSON object. Anyways, as I didn’t learn my lesson, I started saying I couldn’t relate to assignments, classes and exams to Jason who was still in Diploma.
Nothing much happened as usual, we just had the casual conversation of how certain exploits work during the talks, LinkedIn posts and the amount of people he knew. However, this probably being my last conference I’ll be attending in Singapore for personal reasons, he sure revealed something which ended my last trip to Singapore for conferences with a bang.
In context, I am a purple teamer and Jason… well he’s a rainbow teamer. Basically, he can do everything. So, we were talking about CVEs and Bug Bounty and I asked whether he found any good bugs. Well, he revealed that he found an Account Takeover Vulnerability in an adult website for 7000 USD.
Jason: I can get into anyone's account but I can't post it on LinkedIn, I don't know what to say...
Me: You can caption it with "I can get into anyone's account, but I can't get into anyone".
Wing Wing Arrow

So, what has 2 wings and 1 arrow? A Chinese telephone, wing wing arrow? (ring ring hello?). Besides the talks that was happening, there were a few villages present there. One of it was the radio hacking village or in their own words the Singapore Amateur Radio Transmitting Society. There was an activity that was going on which I was subject 0, where we have to track down a transmitter with the antenna looking device in the photo. So to know whether you’re on the right track, the device will emit a sound the nearer you are to the transmitter.
So there are 2 strategies according to Ragul. The first one was to track it like a metal detector where you wave it around and based on the sound, you go hunting for it. The second method which was much more strategic, you go to the corners of the room and try to triangulate the location of the transmitter. Overall it was a fun experience going on a treasure hunt.
Car Hacking On Crack

I don’t know why, but I feel like people are getting more and more into car hacking. Even big boss Yik Han aka Trailbl4z3r is getting into it. Anyways, you heard of Shiau Huei, you heard of Alina Tan, let me introduce you to one more, Peng Fan! One of his notable CVEs is from Tesla, so he’s the real deal. However, this talk unlike the workshops and sharing sessions done by the people mentioned is a research. What does that mean? Well, that means it’s car hacking workshops and sharing sessions on crack.
Before I continue, I have complete confidence that the presenters and researchers know what they’re doing. However, me being inexperienced at travelling the world found it difficult in catching their accents. Having that said, whatever that I write from here about the talks are just what I saw on the slides. So, what I explain might or might not be true.
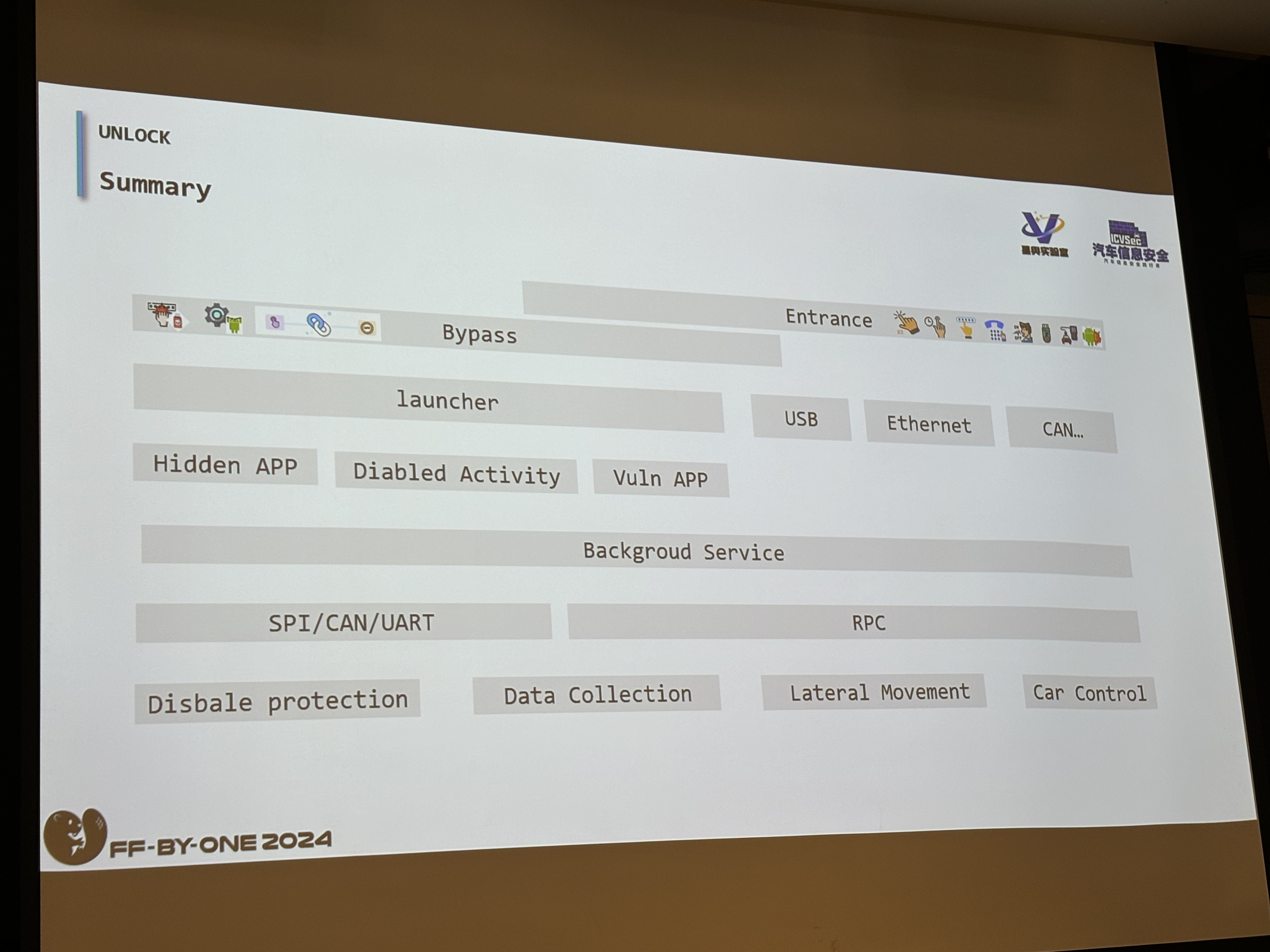
Basically, they started from the surface where normal users or drivers can interact with the car, the car interface or in simple terms or for the younger audience, the iPad in front of the car. They used several techniques to gain access to the services within the car.
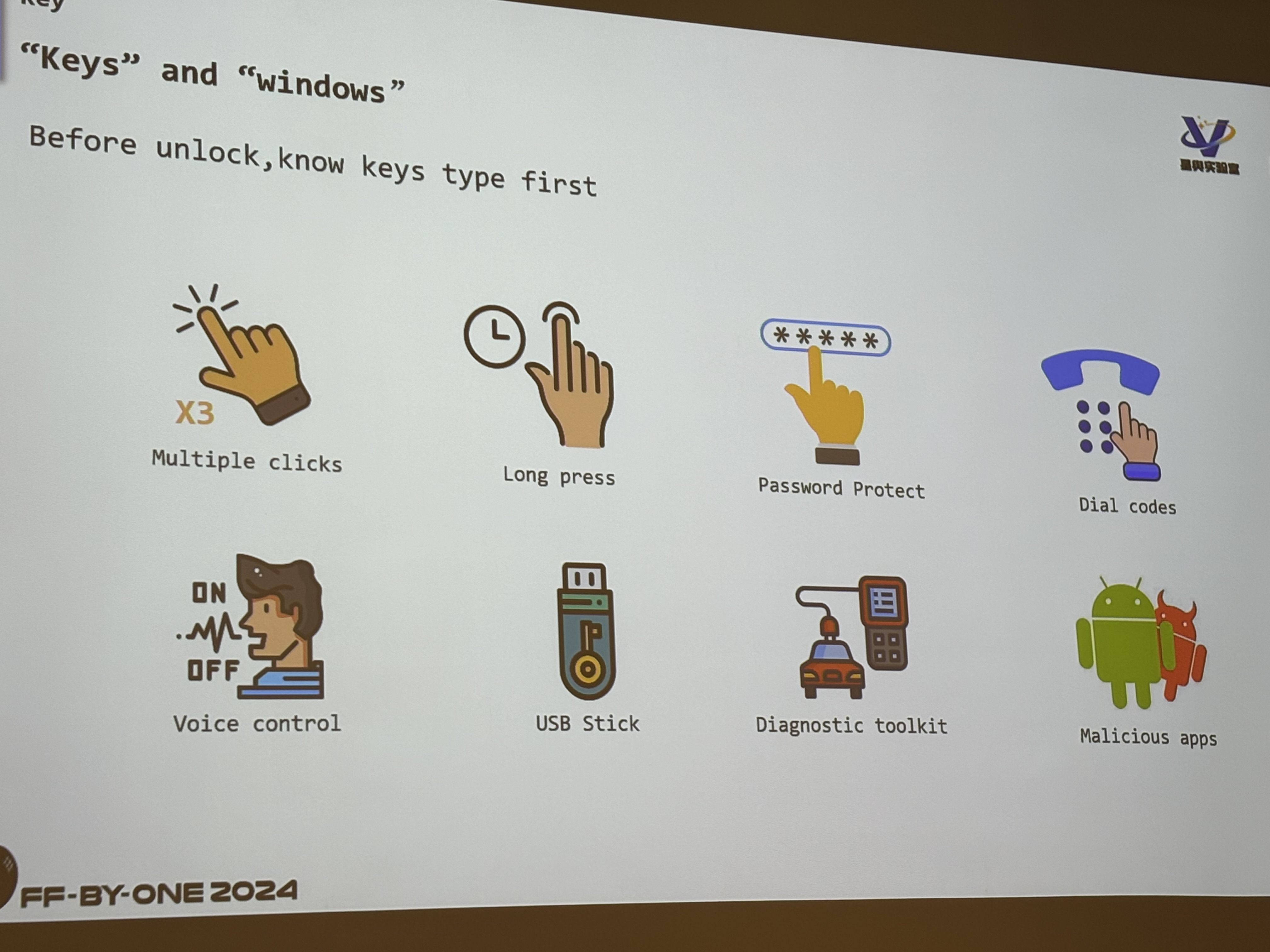
Basically, to gain access to some of the controls of these services, you can perform the actions in the slides shown. The newest techniques that is seen was the voice control method where users can access the debug interface of the car through their voice.
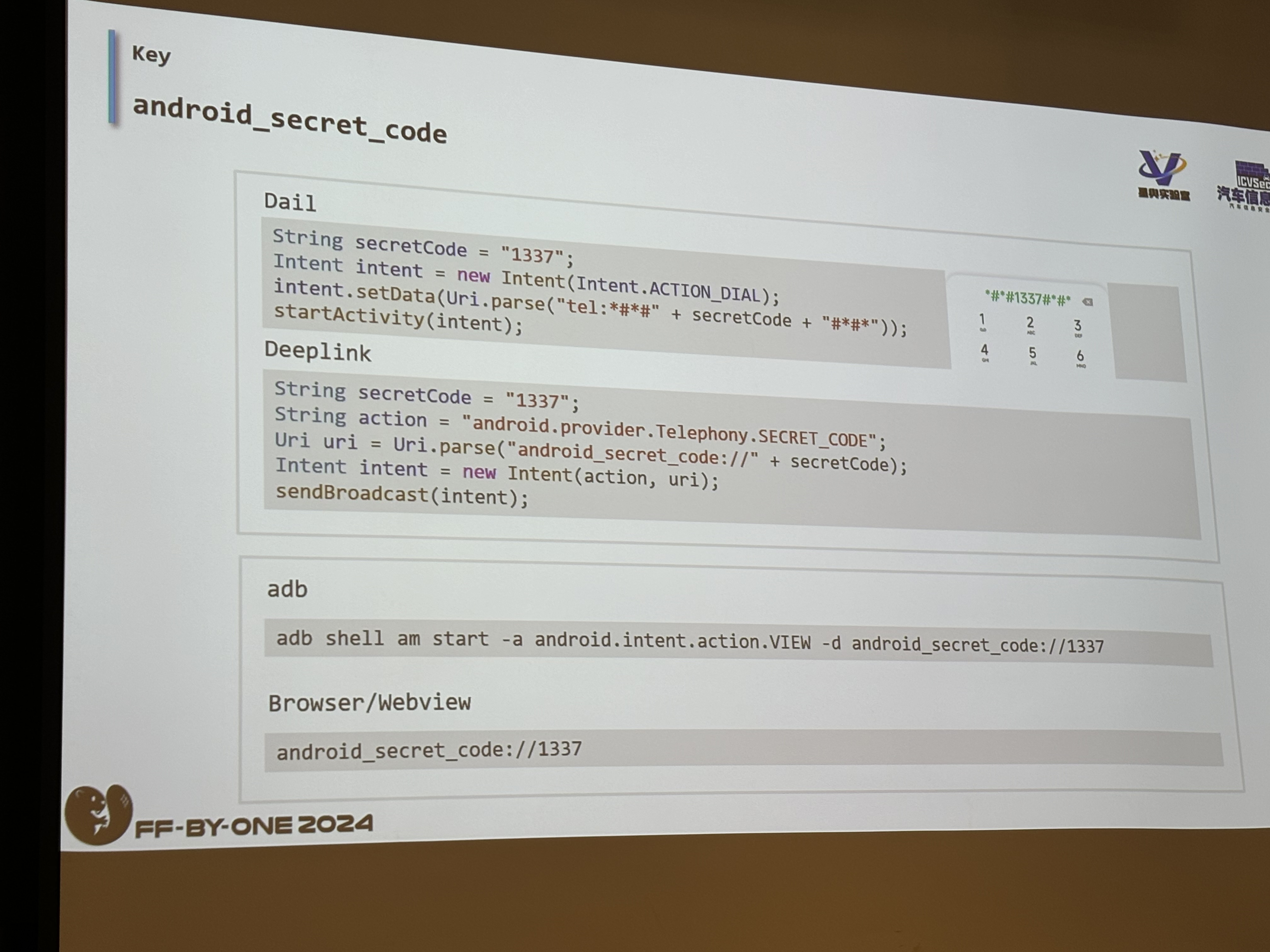
One of the interesting ways that I heard was through secret codes. You know those dial codes on your phone back in the good old days? Oh yea, some of us are young… BASICALLY, you can call a number on your phone to reveal or access certain services. So, in the context of a car, you can dial those codes through the Dialer App, the Deeplink interface, adb and Webview.
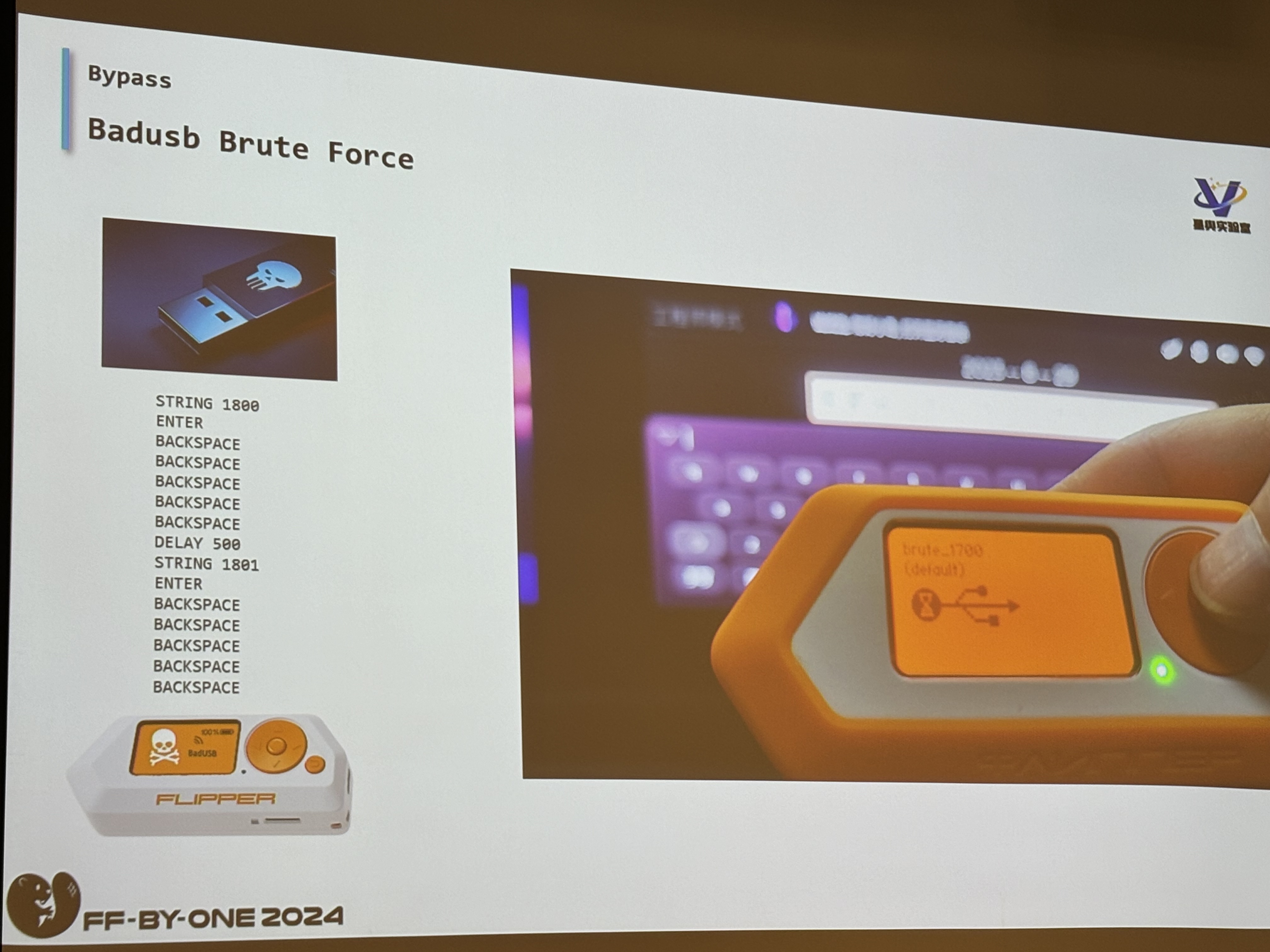
Another interesting way that the researcher found, is to access the engineering mode. However, some cars will implement a passcode so that only engineers can access that interface. So, for this Peng Fan basically used a Flipper Zero (THAT’S CRAZYYY) to perform a BadUSB Brute Force Attack on the car, and the car? Well, it has no protections against brute force attacks.
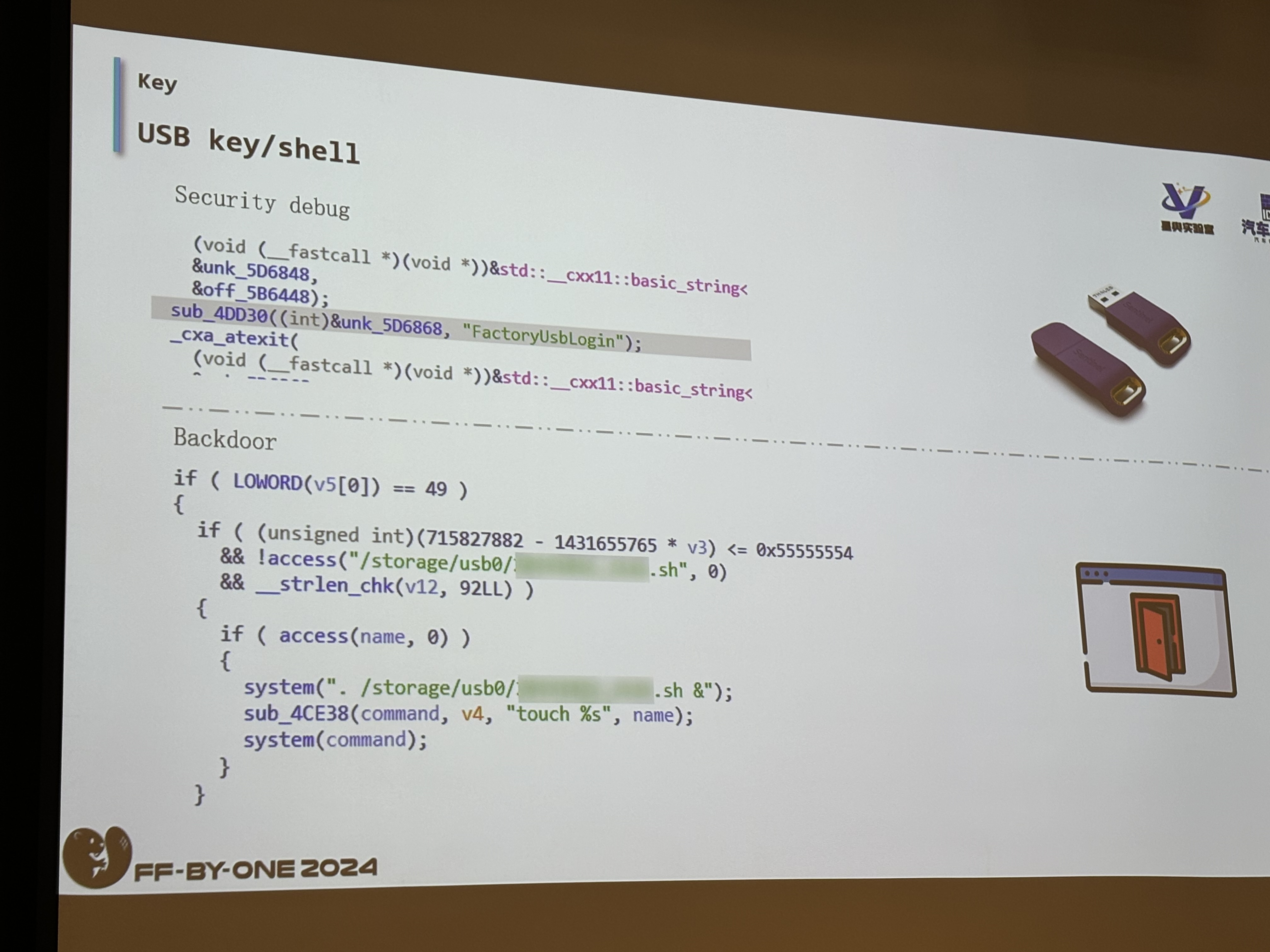
The last method is pretty interesting even though I don’t know what it does, but according to the slide, it looks like they injected a backdoor into the car through a BadUSB. When the researcher finally gained access to the car through the above methods, he could enable services such as adb, and ssh! I didn’t know ssh existed in a car but like the company SNYK, So Now You Know! When those services become available, the researcher can basically control the car!
I Won’t Can’t Break Into Houses

So, I was in Malaysia’s Cybersecurity Camp and BlackHat Asia 2024! Guess what were at those events? If you guessed lockpicking, you were correct! I had every opportunity to learn and “pick” up a new skill. However, quoting from John Wick, I had every chance, every opportunity but I didn’t because… I don’t know… not enough DETERMINATION.

Anyways, there were 2 activities that were going on at the lockpicking station/village. A speed lockpicking competition and a lockpicking challenge to unlock a box. The person who can unlock the locks the fastest or the person who unlocks the challenge box wins a set of lockpicking tools!
Given the opportunity, I went and try unlocking the box with no success. Having that said, I spoke with the dude at the station. Okay, let me mansplain a bit. Most of the time when men talk, we will basically talk until the cows come home without exchanging our names until the very end. Or I could be ************ I don’t know, but we exchanged names on the second day. Anyways, I saw a mysterious tool there, A FREAKING DRILL.

Basically, the dude said that this drill is used by most locksmiths because it’s quick and efficient. HOWEVER, you might be thinking, can we use this to unlock the challenge box? Yea, the dude basically put it this way:
the dude: it's like you having the cheat code and using it to win the prize.
Sacrifices Had to Be Made Again

Another highlight was the hardware station where we could buy a PCB board and solder LEDs onto it to display our names! That was when I met Manzel, the hardware sifu from StarLabs! He was pretty cool as a teacher, guiding me every step to build my name with LEDs. BUT! Of course there’s a but. WHY ARE THERE SO MANY LEDS AND COMPONENTS?!?! Oh yea, one more thing, the board limits us to only 3 letters, so from today I’m known as Zac lol.
In context, there were only 3 soldering irons, not a lot of space and a lot of people. So, we had to either take our turn to complete our board or wait. So, as I wasn’t wanted by the FBI, I waited until I got to build my board. Anyways, when I got to build my board, there was a talk going on by Eugene Lim! I was actually quite curious who was he because before coming to Singapore, everyone was whispering to me, Eugene Lim… Eugene Lim… Eugene Lim…
Anyways, I learned that he was a DEFCON speaker and one of the two OSEE holders in Singapore, I was like crap damn it I missed it.

At the end of my build, Manzel was asking me how was the event and apologised for the long wait. Well, if anyone from StarLabs is reading this, despite having to wait for my turn to solder my components onto my board and taking turns in using the soldering iron, if your activity is that interesting and engaging, it is worth it and you won’t feel cheated of your time. That’s uhhh more than I can say compared to the conferences in Malaysia.
Reveal Yourself MCC Peeps
So, anyways I met Mr Yapp, along with Sarah and Alysha! Finally, I found out who was sponsored by RE:HACK. I’m pretty happy that they were there, seeing how my other friends were no where to be seen (what are friends for am I right?). Most of the day, I would be talking with Sarah and Mr Yapp because the talks were quite difficult for me to understand. But yea, I met the MCC peeps and also gotten a photo with them!

Day 2: Networking Skills Got Nerfed
Alright, for those who don’t know me, I’m Zach! Nah, I’m just playing but for those who don’t know me I can talk to a lot of people about a lot of different stuff. I can talk to you professionally or in most cases I can talk to you very casually. I have slowly learned the skill of conversation threading through many mistakes and many awkward moments in meet ups and conferences. However, I don’t know what happened to me in this conference but my skills went flying out the window. Maybe it was because I was sick during this conference… (was that sign that this conference was toxic? Nonononono, StarLabs I <3 you! HAHAHAHAHAHA). Anyways, the conversations I had were VERY VERY VERY awkward because of me, and I may have embarrassed myself but hey I’m not that important to be remembered!
Awkward Sial

So, the first awkward thing that happened was at the RFID Hacking booth. This booth was managed by Dennis and he represents his company that manufacturers products made by RRG or the RFID Research Group. They sold Proxmark 3’s, Chameleon Ultras, Chameleon Lites, Flipper Zeros, USBNinjas and RFID Detectors there for a discounted price. Roheen wanted the Chameleon Ultra so he contacted me to help him buy it.
As Dennis’ colleagues were helping me pack the items, I had a chat with him. I was wondering whether I could have his contact number so that I can get those products at a discounted price. Unfortunately, he said that those prices are only available in conferences. He also mentioned he has been to BlackHat Asia, BlackHat USA, HackInTheBox (HITB) selling these items. When I heard HITB, I was like:
me: ah cool! So, you'll be in HITB this year too?
Dennis: I'll try...
Another thing that was interesting on the second day was that I noticed that all the Flipper Zeros were sold out and I mentioned that to him! He said:
Dennis: yea... those sold out quick... my buddy who went to BlackHat USA with 500 units with a higher price than usual sold all of them in one day
me: poggers
Anyways, here are the pictures of the things that I bought:


Wait what Zach? That was awkward to you? Uhhhh no. Remember when I said men usually exchange names at the end? Yea, I didn’t with him. So, in the middle of Belinda’s busy schedule, I interrupted her to ask her what was the guy’s name which I didn’t know at that time. She said “Dennis” to me and as if God wasn’t done punishing me, here comes Dennis walking towards us and I’m like:
me: ffs man, God I know I'm a bad kid but come on!
Belinda: Hey Dennis! Meet Zach!
Dennis: Yea! I've met him, he bought a few stuff from me!
Not awkward enough? Alright, round 3. You can see why this gets a bit awkward, where I kept going back to him for sOmE reason. Anyways, Sarah asked me whether it was safe to bring back the Chameleon and USBNinja on flight and I was like:
me: let's go ask the source!
Bad idea… Bad idea… So, me being the dumbass went back to Dennis and ask him just that. He said that he never had a problem bringing Proxmarks and Chameleon Ultras along with him which he always have. However, he did have a problem in Dubai because it was illegal for him to sell it there. In the end, he said if they ask just say that it’s for our work or job.
Zach Meets Zach
Ah another day, another try at the lockpicking challenge! So, for the second day, the dude dumbed down the lock for us. So, while I was picking the lock, I had a chat with him again! I was wondering where he picked up lockpicking and this was his story…
He once had something precious taken away and hidden from him by his mother. His mother locked up his precious thing away so that he couldn’t get access to it. So, he being inspired by movies, decided to use a paper clip to unlock the drawer that had his thing in it. He said that wasn’t his origin story but that story stuck with him.
Anyways, I also mentioned they had this during BlackHat Asia 2024, and this dude decided to just roast me.
the dude: why didn't you make the connection that we were there?
me: because I didn't think of it?
Well at the end of the day he said he was going to tell his team that there was this joker at Off-By-One who didn’t make the connection that they were at BlackHat Asia too. Awkward Counter: 2.

Well, seeing that I was at his booth for a long time, he decided to dumb down the lock again. Through brute forcing the lock, I unlocked it and gotten my first locking picking set! This set off some questions from me. Without sounding ungrateful I asked whether the lockpicking set were cheaply made. This was our conversation:
the dude: well I tested a lot of lockpicking sets and embarrassingly enough I gave away those cheap ones sold on Shopee in conferences
me: damn...
the dude: but through experience, I learned what to buy and what not to buy now
me: what a journey!
the dude: yea, when I first started in HITB SG, there was just one lock and one lockpick but now we have all of these!
See what I freaking mean??? Even though costs are a concern in conferences, this dude and of course kudos to the organisers, tried to give an experience to the people who come to these kinds of conferences. Yea sure it may be small and visually unimpressive, but it gave an experience to the participants and they wouldn’t feel cheated of their time. So, it was kinda cool that this dude made it in the long run.
Well, at the end of the conference, I finally got his name, and it was Zach. Exactly the same spelling and pronunciation. So, Zach met Zach. One of which permanently increased his lockpicking skills through this Fallout Bobblehead.

Am I An Introvert?
So, this was the last interaction I had with a stranger and funny enough it was Manzel! Well, after I met Manzel at the hardware station the first day, I was quite curious about him. Being a stalker I mean a purple teamer I went to LinkedIn to stalk him, I mean to gather intelligence on him lmao. So apparently he was in GCC 2024, which made me had flashbacks to my interview with SherpaSec. Now, in context, for GCC 2024, the method of qualifying to go to GCC for Malaysians was through a selection phase and an interview phase. Obviously, I failed the interview phase, but we don’t talk about that.
However, in Singapore’s case I heard that they sent the same people every year, so being the dumb and apparently introverted person as I am (having my social skills thrown out the window), I talked to him about GCC. For real, I wished I could’ve had beer (which was my magic talking potion) at that time which was available but I had stomach problems remember? At that moment, I was like Homer Simpson in this scene.
Basically, there were a few awkward pauses as I was trying to think of the next thing to talk about. However, this was what I was able to come up with. I asked whether GCC was a good experience for him and he said yes because he was able to meet a lot of people from different countries and in terms of the workshops there it was interesting for him as he was able to learn more about the Blue Teaming side. Of course, I asked whether it was his first time in GCC which he replied with yea. So, in summary, I was lied to by my own country man.

Anyways, after the awkward GCC talk, I moved on to another awkward talk about work. As mentioned before, Manzel worked in StarLabs. Apparently, he has been working there for about a year as a hardware researcher. He explained he basically takes IoT devices and dump the firmware from it and reverse engineers it to find vulnerabilities, which was pretty cool. That’s when I learned that he made the electronic badges for GCC 2024 and as well as the badges for Off-By-One! I feel like I should have known that, but as mentioned before I gave up hope that I’ll be going to Off-By-One until the last minute so I didn’t pay much attention to the posts on LinkedIn. He then asks me what was I up to, and I basically said I was job hunting. When asked about what I specialised in, I said I basically specialise in Red Teaming, Blue Teaming, Malware Development and Malware Analysis. He was quite impressed about that, I hope lol but yea here I am without sleep and 3 cups of homemade coffee…

Kena Lockup

Aiya I kena lockup… by listening to a talk about chaining CVEs baby!!!

Anyways this talk was mainly by JeongOh Kyea, one of 3 researchers involved in this research. This research involves sandbox escapes and multiple privilege escalation vectors involving kernel vulnerabilities to gain NT Authority System on the host.

As I didn’t really understand the talk that well being unexperienced, I understand that they used JavaScript to escape the Chrome V8 Engine sandbox to become a user within the guest operating system and through kernel vulnerabilities within Windows, they got NT Authority System on the guest operating system. They then abused VMWare features to escape the virtual machine to the host as a user and through kernel vulnerabilities again, gained NT Authority System on the host machine. They used a couple of CVEs, a couple of Pwn2Own exploits, some of which were found by StarLabs themselves!
Conclusion

I’m going to end this blog off by once again thanking Belinda, because she didn’t have to help me but she did. I think by helping each other out within the cybersecurity community like this, especially students like me (I know I’m about to graduate but my point still stands damn it), will benefit the community as whole by sharing our knowledge and experiences. Lastly, as it may be the last conference I’ll be going to Singapore, this was still a new and fun experience to me, better than the conferences held in Malaysia. Even though I might want more stations (and I don’t have any recommendations as I’m writing), I know there might be budget concerns or the trouble of getting people but as for now, it’s REALLY REALLY REALLY good in my opinion.


Here’s a flag for making it to the end:
flag{BY3_bye_51NgApORE}