
So I participated in a CTF alone??? Yes I did! Ending 2023 off, I participated in Wargames 2023 in the student category! And oh boy for this writeup it was the King of Forensics vs the God of Forensics. However, I did learn something new today from one of the God of Forensics. With that said, let’s get into the writeup!
The challenge was called “Compromised” and it provided a file called evidence.zip
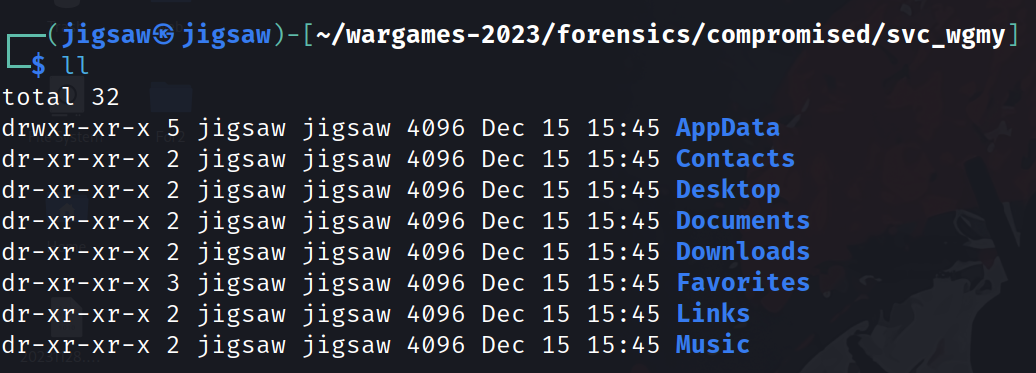
Unzipping the file, it contains a service account’s file system. However, all that remains is ALOT of lnk and ini files which are useless.
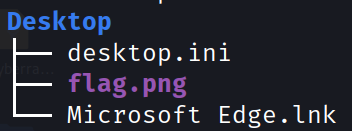
One of the noteworthy files in the Desktop folder is flag.png.
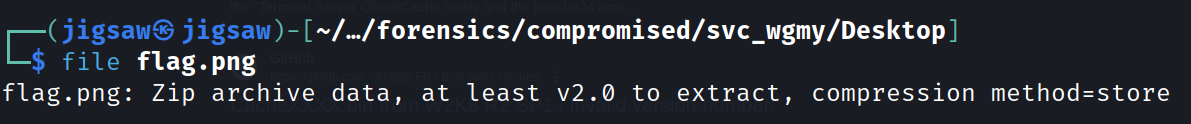
Using the file command on it, shows that the file is actually a zip file with a store compression method. From this point, I went into a rabbit hole thinking that I need to use bkcrack to brute force the keys for the zip file because of the store compression method.
You can watch John Hammond’s video on that here
Going into Documents you can see a Default.rdp file, which means that this machine has been accessed before through RDP.
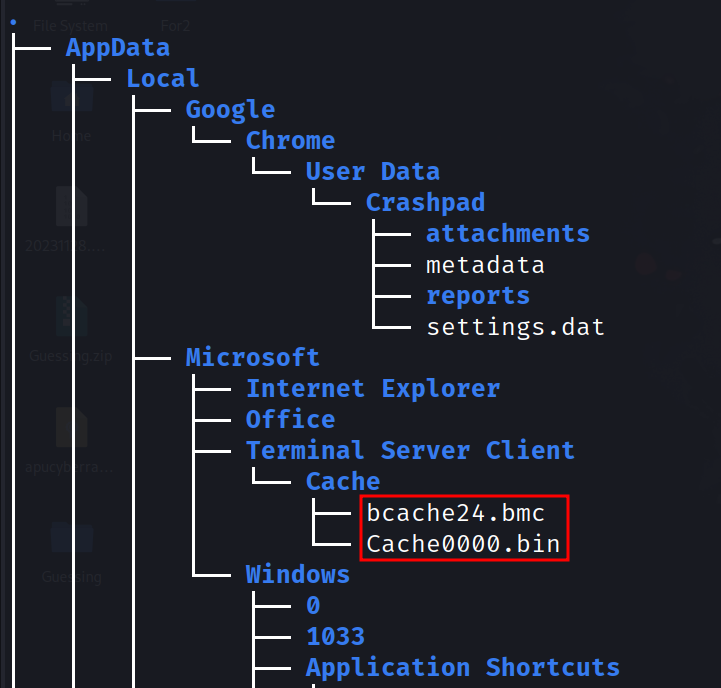
Going all around the file system, I eventually came to this directory:
svc_wgmy/AppData/Local/Microsoft/Terminal Server Client/Cache

I was wondering what were those files in that directory, those files being bcache24.bmc and Cache0000.bin.
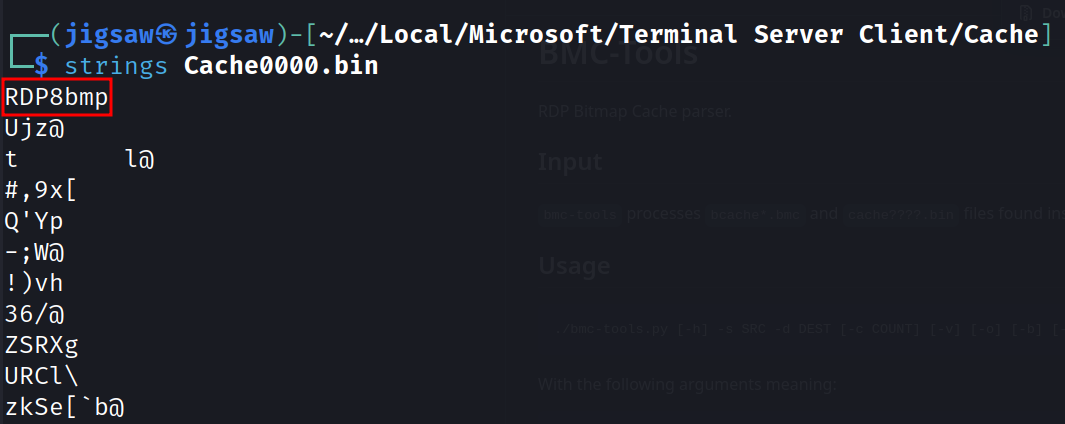
Using the typical Forensics mindset, I used strings and found that it was a bmp file but not?
I decided to look up the file name and miraculously I found a blog post on this file regarding… FORENSICS!!!
Apparently, the file is a cache file of images taken as a result of RDP. The files are cached first and then sent to the client (from my understanding of how RDP works). The blog post then demonstrates using bmc-tools.py to parse the cache file.
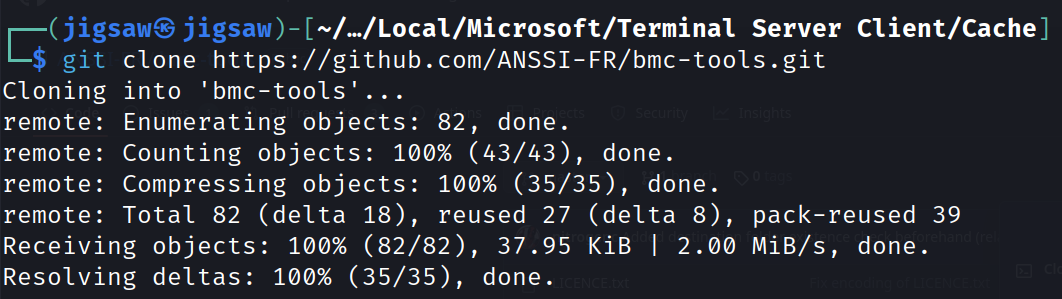
So, just clone this repository:
git clone https://github.com/ANSSI-FR/bmc-tools.git
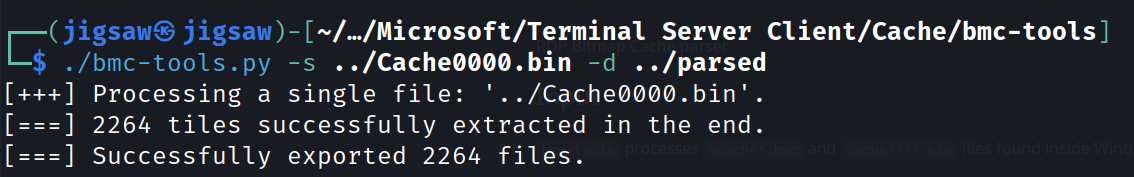
And executing the files with the -s switch for the source of the cache file and -d for the destination of the bmp files.
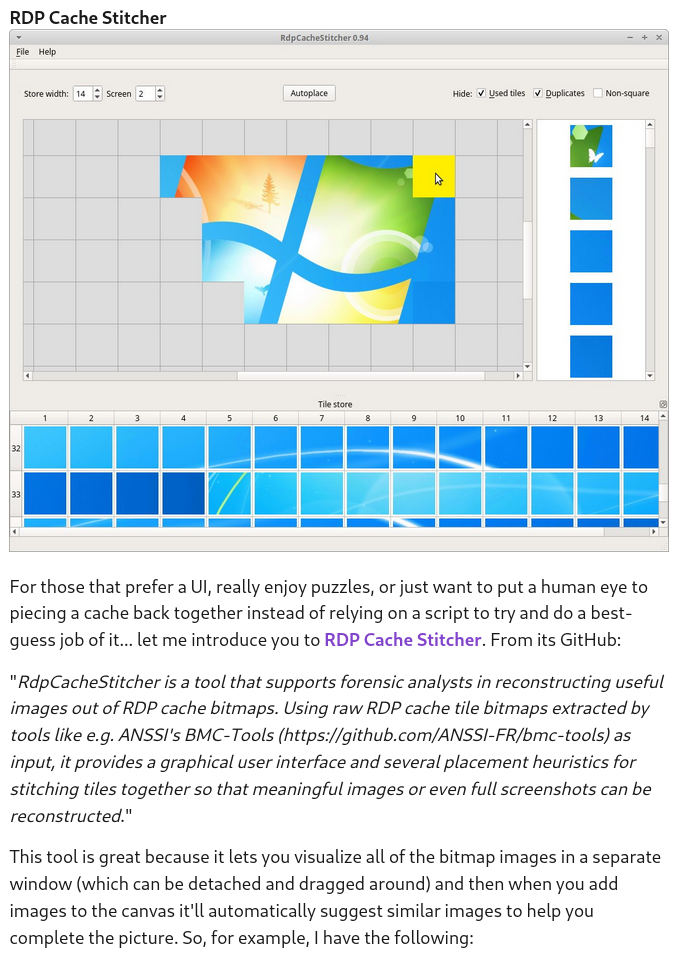
So, we got some bmp files, what now? Well, the blog post mentioned there is a GUI tool to piece the puzzle together.
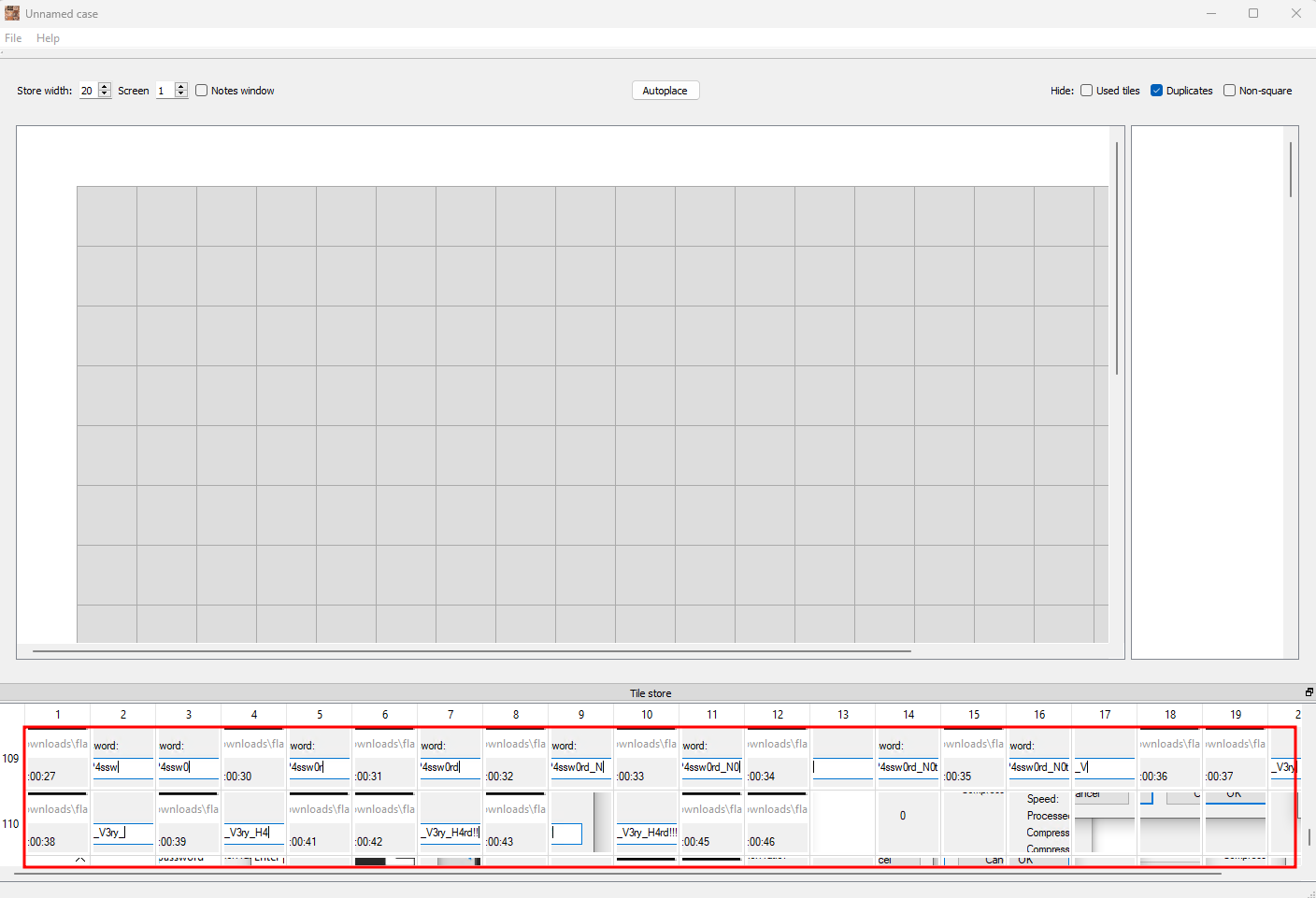
Loading the bmp files into the tool and scrolling through the images, I saw a few images of a user typing in the password for the zip file.
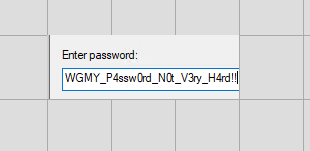
Selecting the right images and piecing them together, we get the password!
WGMY_P4ssw0rd_N0t_V3ry_H4rd!!!
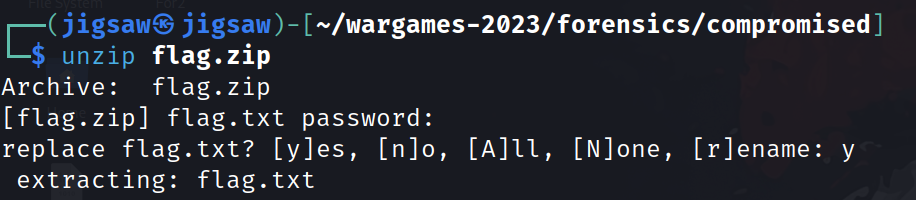
From here it’s just as easy as cake! Unzip flag.zip and cat out the flag!

Sheeeeshhhhh I might be good at Forensics but sometimes or most of the times I may not know everything. So, it was a good learning experience from this challenge of the many artifacts you can find from Windows and yea I will totally take note on this challenge. Who knows? I might make a challenge based on this… Anyways, here’s the flag!
Flag: wgmy{d1df8b8811dbe22f3dce67ef2998f21c}