So another writeup for another Forensics challenge for Wargames 2023! I ended the year off with a PTSD challenge as usual with any CTF I had. This time it was a challenge I was very familiar with after seeing this type of challenge in PicoCTF but I was concentrating on the wrong things. With that said, let’s get into the writeup!
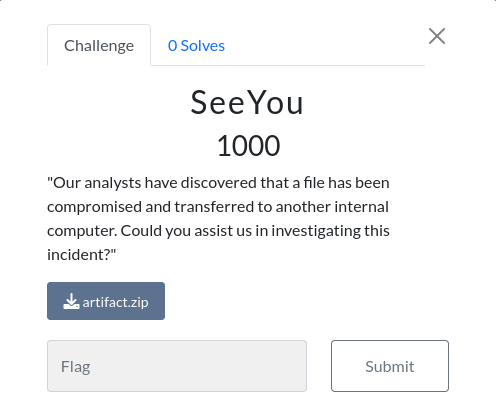
So, we can see here that a file is provided to us and that the description of the challenge mentioned that data has been exfiltrated through the network internally.
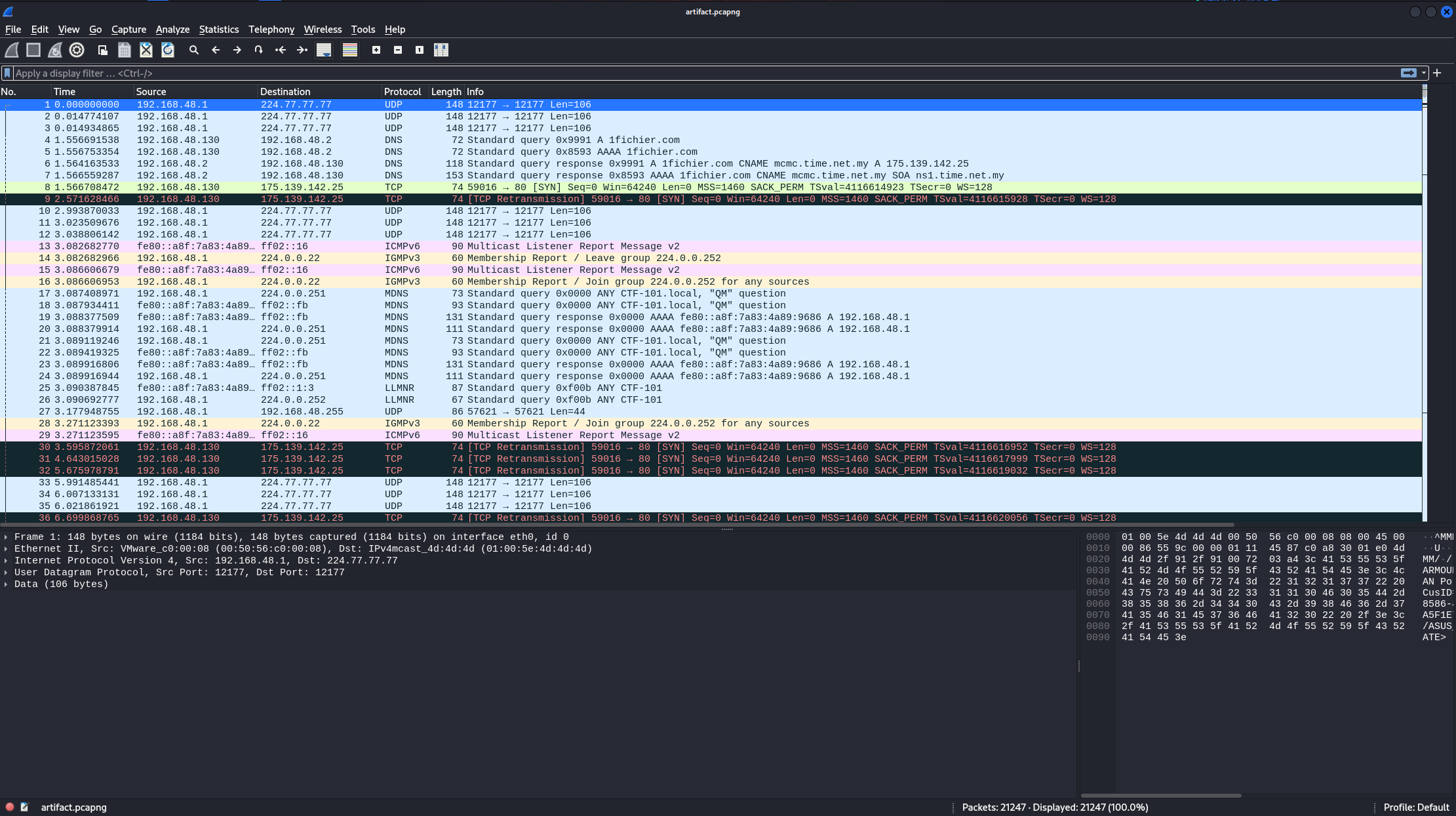
Extracting the zip file gives us a pcapng file which when opened, revealed a bunch of packets. However, sticking to the description of the challenge, I started looking for IP addresses.
I managed to stumbled on this, connections from a machine on the same port to different ports on a different machine were being performed.
Immediately, I started Googling for TTPs about this kind of exfiltration and I came up with this whitepaper from SANS.
By the way, I was so deep into this whitepaper that I started reading the source code of the tool.
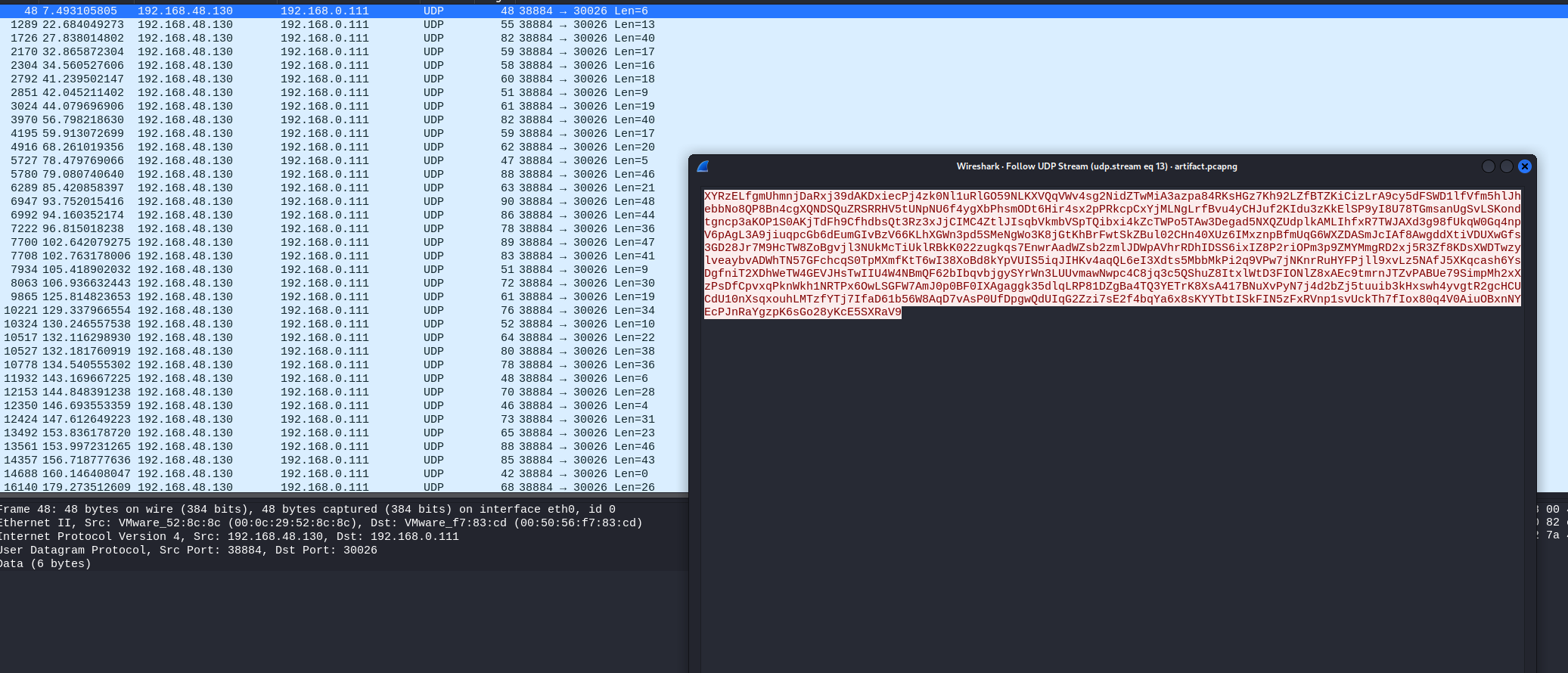
Now, starting from here, my downfall begins…
From previous packet analysis challenge, and as a habit I check for data within streams and coincidentally there was data within the packets. I started writing scripts to extract all the data from the packets that were going to their respective ports, arranging them from 30000 to 30255 and decoding them using base64, base62 and base32.
When that didn’t work, I tried arranging them based on timestamps, which didn’t make sense because Wireshark does that by default. Basically, I was in a rabbit hole.
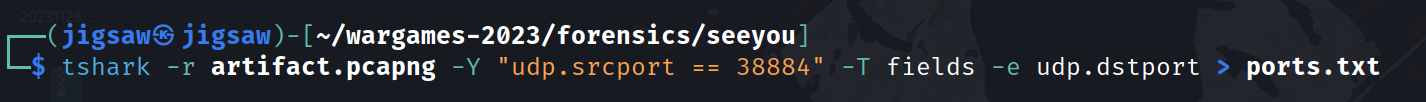
tshark -r artifact.pcapng -Y "udp.srcport == 38884" -T fields -e udp.dstport > ports.txt
After the CTF ended, I discovered I was suppose to look at the ports! So, I made a tshark query to do just that and output it to a file.
#!/bin/bash
# Check if a file name is provided
if [ "$#" -ne 1 ]; then
echo "Usage: $0 filename"
exit 1
fi
# Process each line of the file
while IFS= read -r line; do
echo "$((line - 30000))"
done < "$1"
Furthermore, since I was concentrating on the ports, I needed to minus the front part of the ports which was an offset of 30000. So, again… I wrote a bash script to do just that.

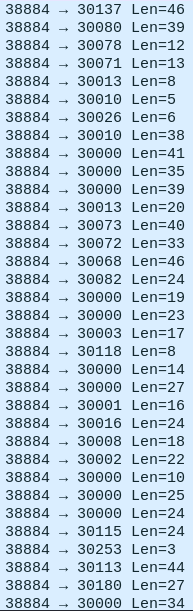
And the result was this blob.
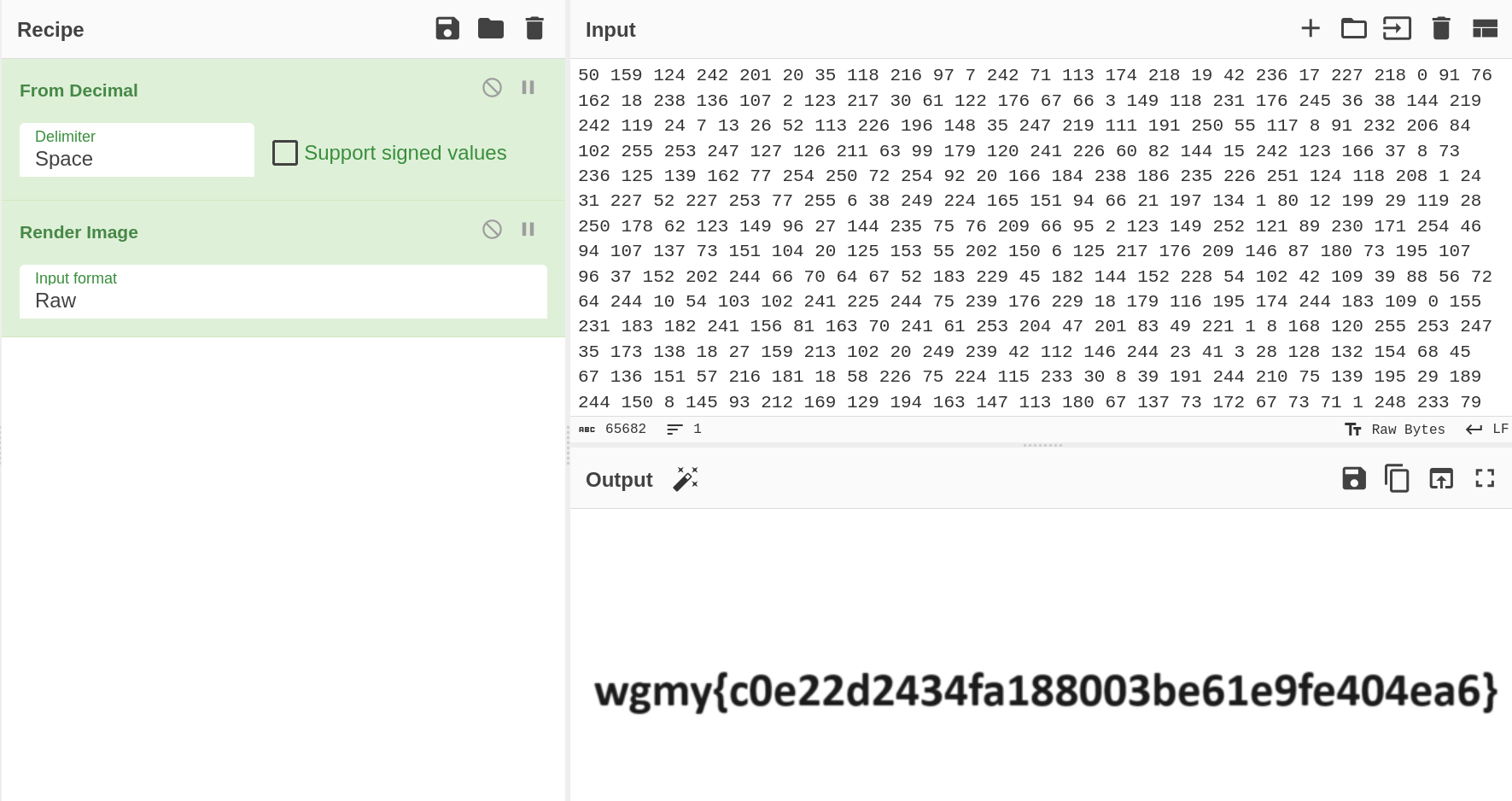
As I did this kind of challenge before on PicoCTF, I knew the values were in decimal. So throwing it into CyberChef and placing the recipes From Decimal and Render Image gives us the flag!

A place to scream: AHHHHHHHHHHHHHHHHHHHHHHHHH
Anyways… here’s the flag:
wgmy{c0e22d2434fa188003be61e9fe404ea6}